SecureLink - An SSH Client built from Scratch
Abstract
Abstract
Mentors :
Calisto Abel Mathias (+91-8861257917)
Shishir Hegde (+91-7090875935)
Mentees:
Nischay Bharadwaj Mahesh(+91 9980543867)
Dhruv Mohan Anand (+91-9779450099)
Shashank Shreyan Pazhani (+91-9611537208)
Ronak Maharia (+91-8824113465)
Manish M Dev (+91-8197059167)
Rithesh Prakash Bhagat t(+91 70471 00480)
Github Repository : https://github.com/N-tronics/sshclient
Google Meet Link : https://meet.google.com/cyg-gsdj-qmh
Aim :
The aim of this project is to design and implement a secure SSH client and server in C++ from scratch, adhering to the SSH-2 protocol. The goal is to build a working system that enables encrypted communication, secure authentication, and remote command execution using fundamental cryptographic techniques.
Introduction :
This C++ project is a from-scratch implementation of an SSH client and server, built to help you understand how secure communication really works. It follows the SSH-2 protocol and includes features like Diffie-Hellman key exchange and AES-256-CBC encryption. Ideal for diving into cryptography, networking, and protocol design, this project offers a hands-on way to learn the inner workings of SSH.
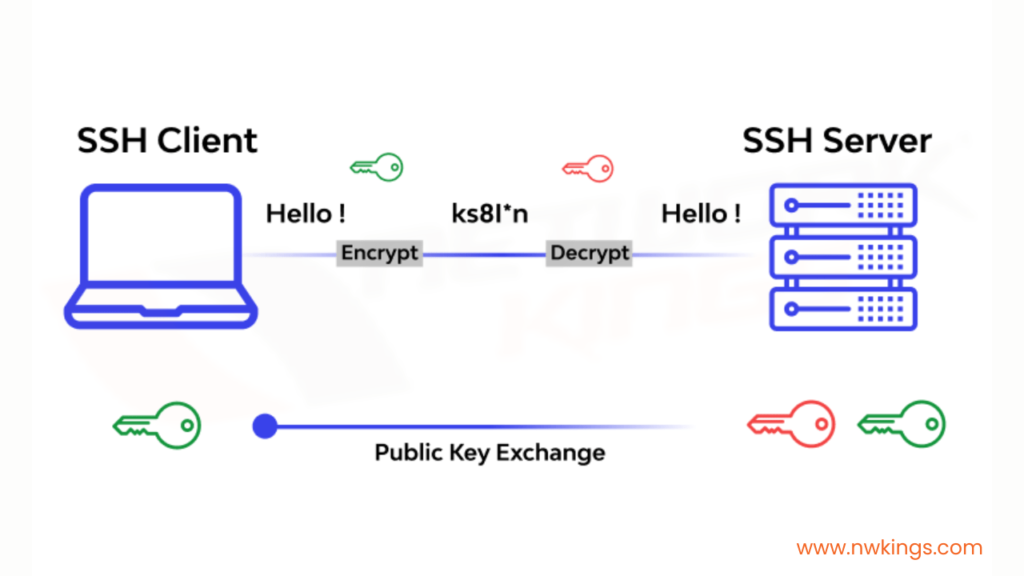
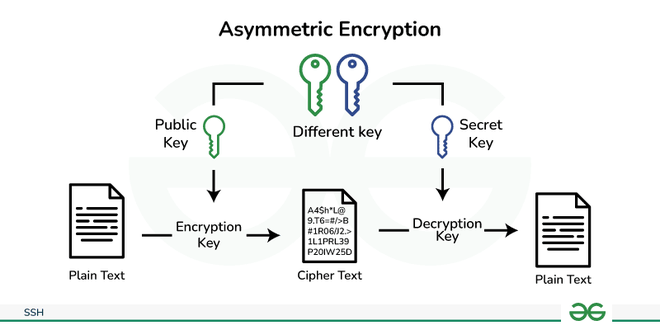
Literature survey and technologies used :
SSH Protocols : RFC 4251, RFC 4253
Elliptic Curve Diffie-Hellman Key Exchange
OSI & TCP Models
Encryption and Decryption using AES-256-CBC
SSH Public Key Authentication
Protocol Design Principles as per National Cyber Security Centre
Tools Used : C++, CMake, OpenSSL for SHA256, Custom Cryptographic Implementations, Linux Sockets API, Terminal or Console-based I/O
Methodology :
1.Diffie Hellman Key Exchange :
- The project uses the Elliptic Curve Diffie Hellman algorithm to calculate a shared secret that only the client and server know. Elliptic Curves use a field in the form of y^2 = x^3 + ax + b (mod p).
- The values of a, b, and p are predetermined with proper mathematical testing to ensure that the curve is secure.
- The RSA algorithm is used to sign an exchange hash, which is calculated using the SHA 256 algorithm, to ensure the identity of the SSH server.
2.AES encryption :
- After establishing the secret key, 3 new keys are derived and used for encryption and decryption of further packets. The AES 256 encryption standard in CBC mode is used to encrypt the messages. The HMAC-SHA256 algorithm is used to authenticate the messages.
- When the server receives a new client connection, it first verifies the protocol of the client. If the client does not follow SSH protocol, it ends the connection. Then, it performs a key exchange to establish a shared secret through unencrypted packets.
- Once the shared secret has been established, the server and client both can encrypt and decrypt packets. Thus, all further communication is through encrypted packets using AES 256 in CBC mode. These packets are authenticated with HMAC-SHA256 codes.
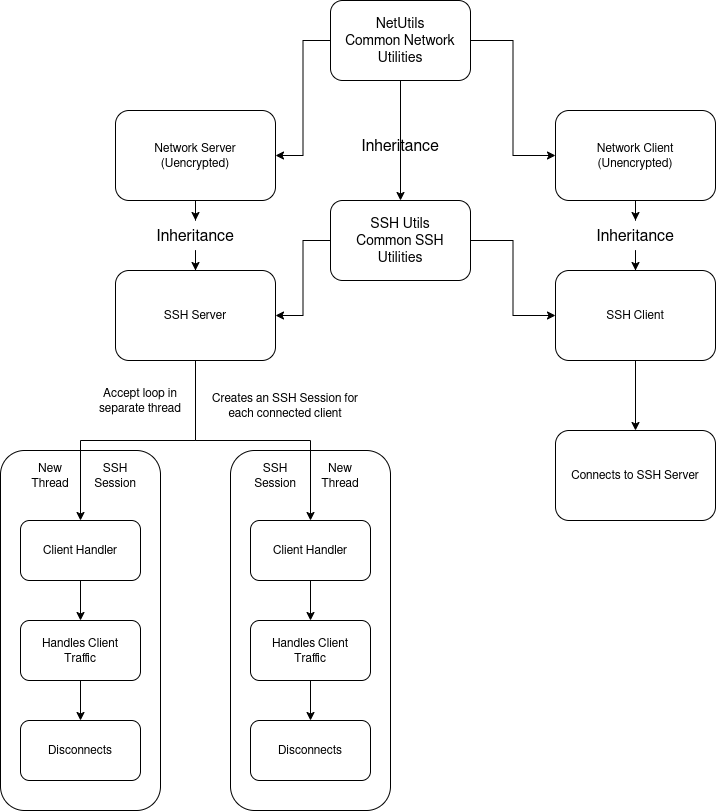
Results :
The system was evaluated through both manual and scripted test cases simulating real-world client-server interactions. Key aspects of the implementation were validated as follows:
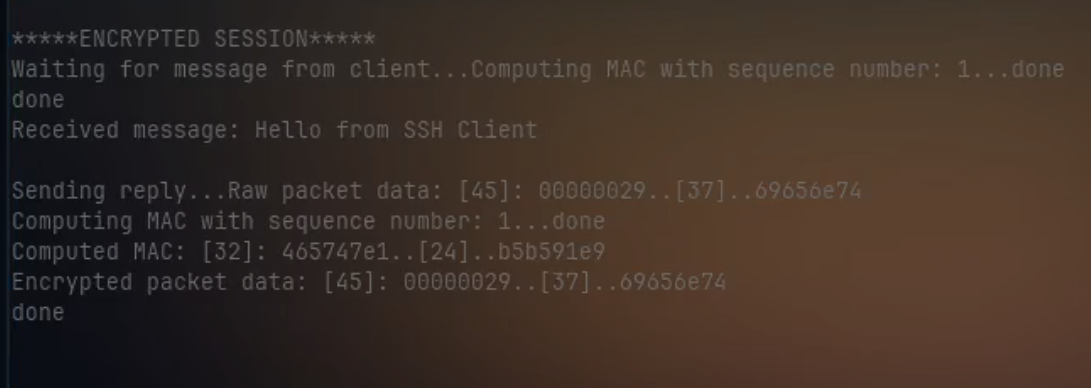
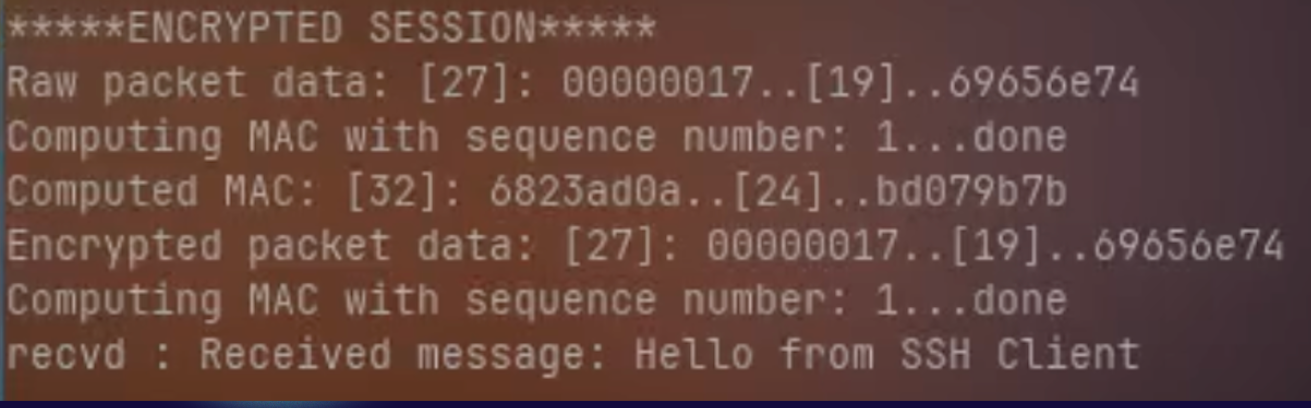
Key Exchange Verification: Logs from both client and server confirmed that the derived session keys matched, indicating a successful Elliptic Curve Diffie-Hellman exchange.
Encryption/Decryption Accuracy: The client-server message exchanges were encrypted and decrypted without data corruption or loss, confirming the correctness of AES-CBC operations.
Tamper Detection: Modified packets were correctly rejected by the receiver due to HMAC mismatches, validating message integrity mechanisms.
Performance Baseline: Despite being a proof-of-concept, latency remained low during transmission of messages under local network conditions, confirming the practicality of the implementation.
Edge Case Testing: The system was also tested under conditions such as:
- Empty messages
- Messages exceeding buffer size
- Loss of connection during communication
- Repeated connection attempts
In all such cases, the application either recovered gracefully or logged appropriate errors.
Fallback to Unencrypted Communication: Tested the system's ability to operate without encryption for comparison and educational insights.
While specific performance metrics were not the primary focus, the implementation demonstrated reliable and stable operation during testing. The encryption and decryption processes introduced minimal latency, suitable for basic secure communications.
Conclusions and Future Scope :
The SSH Client project provides a foundational implementation of SSH packet handling, adhering to key specifications of the SSH protocol as outlined in RFC 4253. Through a modular, object-oriented design, the project introduces a structured way of managing SSH packet creation, serialization, deserialization, and secure padding. The use of abstract base classes such as TCPPacket and its derived implementation SSHPacket illustrates a strong design pattern promoting code reusability and extensibility.
The current implementation is robust for packet-level operations and offers well-defined mechanisms for payload manipulation, padding generation, and byte-level transformations. Additionally, the use of secure random number generation and proper validation mechanisms ensures the integrity and security of the data being handled.
While this project successfully implements the core of SSH packet handling, several areas remain for future development:
- User Authentication Mechanisms: Incorporate support for various authentication methods such as password-based, public key, and multi-factor authentication to enhance security and flexibility.
- Channel Management: Implement SSH channel functionalities to support features like remote command execution, port forwarding, and file transfers.
- Graphical User Interface (GUI): Design a user-friendly GUI to make the SSH client more accessible to users who prefer graphical interfaces over command-line tools.
- Performance Optimization: Analyze and optimize the application's performance to handle multiple concurrent connections efficiently.
These enhancements would broaden the application's capabilities, making it more versatile and user-friendly.
References :
https://en.cppreference.com/w/
https://git-scm.com/book/en/v2
https://datatracker.ietf.org/doc/html/rfc4251
https://datatracker.ietf.org/doc/html/rfc4253
https://www.openssh.com/
https://www.geeksforgeeks.org/c-plus-plus/
https://www.geeksforgeeks.org/socket-programming-cc/
Report Information
Team Members
Team Members
Report Details
Created: May 21, 2025, 7:34 p.m.
Approved by: Upasana Nayak [CompSoc]
Approval date: May 25, 2025, 12:51 p.m.
Report Details
Created: May 21, 2025, 7:34 p.m.
Approved by: Upasana Nayak [CompSoc]
Approval date: May 25, 2025, 12:51 p.m.

